
A fully undetectable (FUD) malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection.
The samples grant “threat actors the ability to load numerous malware families and exploits with ease through highly obfuscated batch files,” Trend Micro researchers said.
About 79.6% of the total 784 artifacts unearthed have no-detection across all security solutions, the cybersecurity firm added, highlighting BatCloak’s ability to circumvent traditional detection mechanisms.
The BatCloak engine forms the crux of an off-the-shelf batch file builder tool called Jlaive, which comes with capabilities to bypass Antimalware Scan Interface (AMSI) as well as compress and encrypt the primary payload to achieve heightened security evasion.
The open-source tool, although taken down since it was made available via GitHub and GitLab in September 2022 by a developer named ch2sh, has been advertised as an “EXE to BAT crypter.” It has since been cloned and modified by other actors and ported to languages such as Rust.
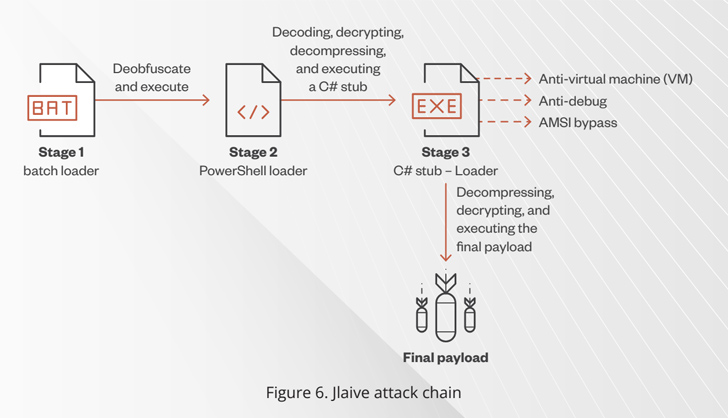
The final payload is encapsulated using three loader layers – a C# loader, a PowerShell loader, and a batch loader – the last of which acts as a starting point to decode and unpack each stage and ultimately detonate the concealed malware.
“The batch loader contains an obfuscated PowerShell loader and an encrypted C# stub binary,” researchers Peter Girnus and Aliakbar Zahravi said. “In the end, Jlaive uses BatCloak as a file obfuscation engine to obfuscate the batch loader and save it on a disk.”
BatCloak is said to have received numerous updates and adaptations since its emergence in the wild, its most recent version being ScrubCrypt, which was first highlighted by Fortinet FortiGuard Labs in connection with a cryptojacking operation mounted by the 8220 Gang.
“The decision to transition from an open-source framework to a closed-source model, taken by the developer of ScrubCrypt, can be attributed to the achievements of prior projects such as Jlaive, as well as the desire to monetize the project and safeguard it against unauthorized replication,” the researchers said.
What’s more, ScrubCrypt is designed to be interoperable with various well-known malware families like Amadey, AsyncRAT, DarkCrystal RAT, Pure Miner, Quasar RAT, RedLine Stealer, Remcos RAT, SmokeLoader, VenomRAT, and Warzone RAT.
“The evolution of BatCloak underscores the flexibility and adaptability of this engine and highlights the development of FUD batch obfuscators,” the researchers concluded. “This showcases the presence of this technique across the modern threat landscape.”




